Choosing which projects to invest in is a strategic decision to be taken based on objective data. In this article, we explore the problem of subjectivity and analyze the solution that allows management to make decisions based on a business plan, in a rigorous and transparent way.
The Problem
In businesses where the source of income comes from making projects for clients, it is easy to decide which ones are to be put in place: (usually) those of greater profitability. And in some cases, all, if sufficient resources are available.
However, internal projects, such as those of transformation, tend to not offer such an obvious criterion as their value to the business is less evident and often more subjective to anticipate.
The fact that an expected value is subjective does not mean that its effects are not going to be real. It means that the benefits are hard to predict, and investment decisions can be based on perceptions.
This is a challenge that managing directors have always tried to address. The most used resource as a solution has been that of the "business case", which requires promoters to express the profitability or value contribution of their initiative in measurable terms, either in sales increase or in cost reduction.
The main difficulty presented by the business case is the human factor: a promoter of an initiative that has a strong motivation to give positive figures and show that their idea is profitable. Though it is desirable to have intrapreneurs on your team it is essential to validate their figures through a homogenous and and objective process.
The second difficulty of requesting profitability to internal projects arises from each promoter having limited vision to their area of competence, defending their plot without considering the overall vision. In turn, management considers these business cases as if they had been generated with the same criteria, which is not usually the case. Each promoter applies with different degree of ingenuity the data to the same template.
The issue at hand is knowing when to recognize, in an objective fashion, what initiatives will bring more value to the business when the projects deliver their expected benefits.
The Approach
When it comes to value, it is not always possible to apply a purely financial standard via project profitability based on forecasts in isolation and in comparison of each other.
- The value contribution of a project to a strategic plan may be broader than profitability, even if the savings or earnings have been realistically calculated. For example, a process automation project can throw modest savings, but positively influence a priority target of customer quality perception.
- Strategic project planning should not consider initiatives in isolation, as the result of the set may be greater than the sum of the parties. It is common for the result of some projects to enable others, and its set to offer strategic value. This is why program and portfolio management exceeds project management.
The strategic management of projects lies in the competence of the management and must be facilitated by the Project Management Office (PMO) to the extent that their objectives are the maximization of value and not only the transversal coordination.
Thus, the strategic planning approach to the composition of the project portfolio should consider two main elements:
- A strategic plan that exposes the objectives of the Organization
- A list of project proposals (initiatives)
With these two elements, we can prioritize initiatives that will order them from higher to lower value, generating an orderly list of approved projects (portfolio backlog).
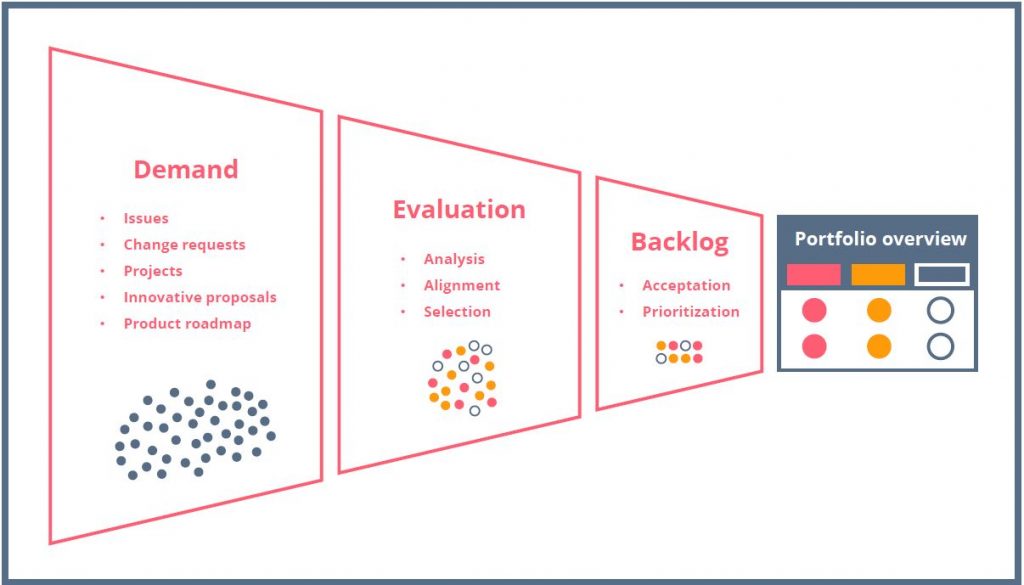
Strategic management of project portfolios
A great advantage that offers prioritization of projects by value is that it supports applying resource constraints as a cut-line to its output. If we have a list ordered by value and – for example-a budgetary limitation, we will be able to establish the approval of projects based on those that contribute more value and that are within the available budget.
The Process
Once we have the two main elements (objectives and demand), we can start two classification processes that can run in parallel or go in sequence. What is important is to isolate each other to ensure objectivity and ease of adaptation to the general standard.
Process 1: Prioritization of Objectives
Participants: Board of Directors
Objective: To put some objectives in front of others, with specific weight of each one on the total.
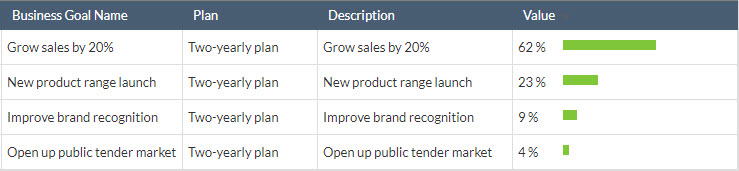
Sometimes strategic plans already specify priorities, but in others they do not give explicit weight by objective. For example, how much more important is "to grow in sales by 20%" than "to increase operating efficiency by 15%"?
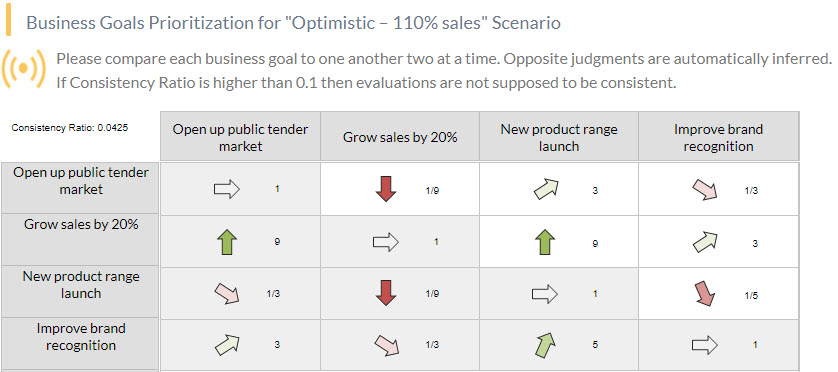
There are several techniques that can be employed to achieve a table like the one above. From something as simple as an agreement amongst the Board of Directors to the most sophisticated such as an Analytic Hierarchy Process (AHP). The latter could be considered more rigourous, though its execution could be simple if you have a Pairwise Comparison Tool, like the one provided by ITM Platform.
This simple table will generate an orderly and quantified list of objectives.
As an added feature, ITM Platform calculates a "consistency ratio" that indicates how logical and objective the prioritization is. In this article, you will find an explanation of how this index is calculated.
It is possible to make different sets of the same objectives through scenarios, and even use different objectives for different programs. The reality is complex and there is not always a single combination or scenario.
Process 2: Contribution of project value to objectives
Participants: The Project committee and promoters
Objective: To determine how much each project contributes to each objective
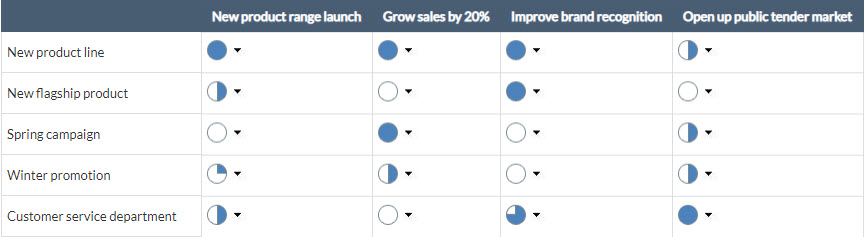
Ignoring for now the relevance of each objective on the strategic plan, this step will assign a weight to the contribution of each initiative to each objective. This weight will be translated to a number base on 100, but if you use ITM Platform you can also use the comparison by pairs previously used or use a qualitative methodology based on ideograms such as the image (Harvey balls), providing a visual support.
Process 3: Analysis of the optimal selection of the Portfolio
The two previous phases provide the necessary parameters for the system to calculate the value of each project, based on 100 and depending on the value of each objective.
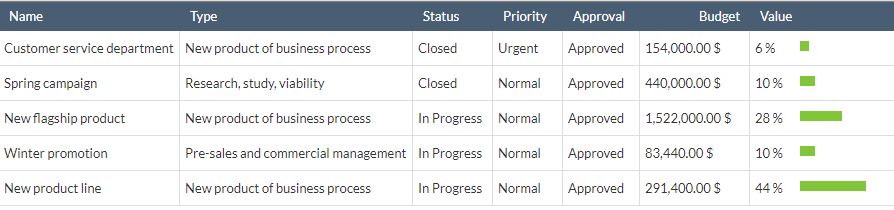
List of initiatives orders by value
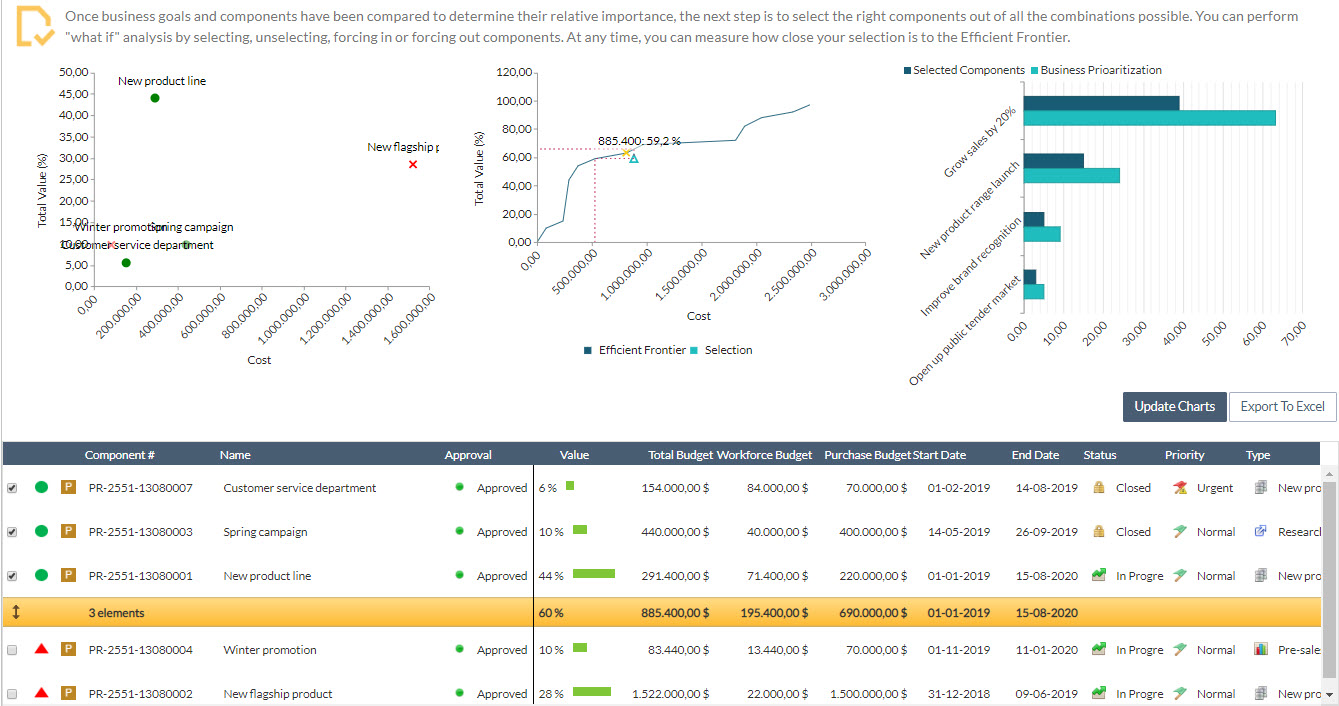
If money wasn't a problem, then we would probably carry out all “reasonable" projects. But in a real organization, the resources available are finite and the previous list of initiatives is not enough to make a good selection of project portfolios.
Thus, it is not only enough to select the most valuable projects, but it is also necessary to filter those that fall within the constraints, be it economic, technical and human resources, or temporary.
In this article, we will use the available budget as an example of a main constraint because this is the most frequent case. Imagine that we should select a portfolio of projects that does not exceed $900.000. Taking the previous list into account, the "New Star Product" ($ 1.5 M) exceeds that amount and also provides a similar value to other more economical projects.
So, with the data we have, we choose the combination of projects that are closer to the available budget: a total of $885.400 and a value of 61% accumulated in three projects.
With this selection achieve the given criteria. But note that the efficient central border graph is indicating the selection is not optimal (value/cost) and that there are better combinations: similar value for less money or greater value for the same sum.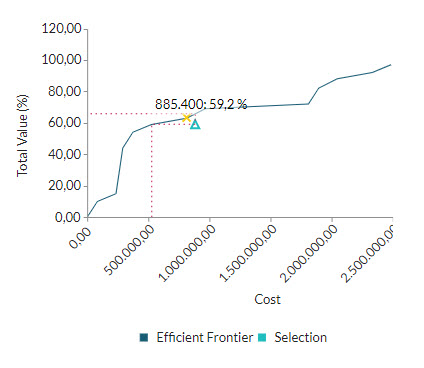
And, indeed, with a portfolio of a total of $528.840 we achieved a contribution of value very similar for 35% less in cost.
If you are interested in understanding how the calculation scheme is made,
Download the guide here.
Conclusion
It is possible to apply rigorous standards in the selection of a portfolio of projects, basing the selection on the value they bring to the business strategy.
Key points to consider:
- A separation of work between the management team that defines and prioritizes objectives, and the teams that analyze the benefits by project.
- A process sponsored by management requiring rigorous standards when making investment decisions and implementing transparency between teams.
- An integrative platform that combines information and exposes the results.
If you want to know more about the management of organizations by projects, download the white paper, where you will learn to:
- Connect management of your Organization with that of projects
- Manage portfolio of projects to create competitive advantage
- Agile Portfolio Management


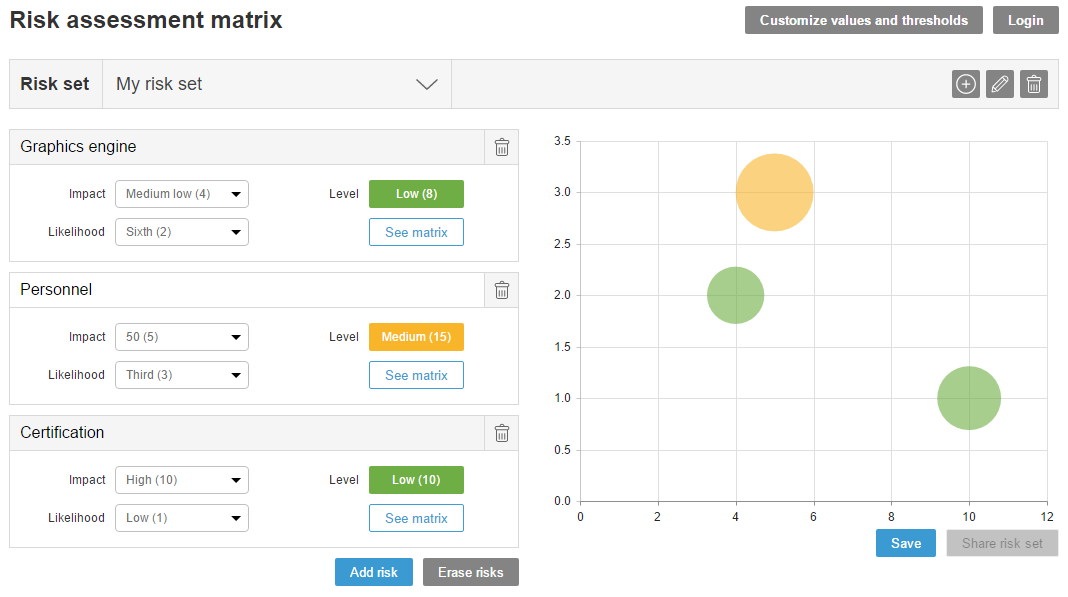

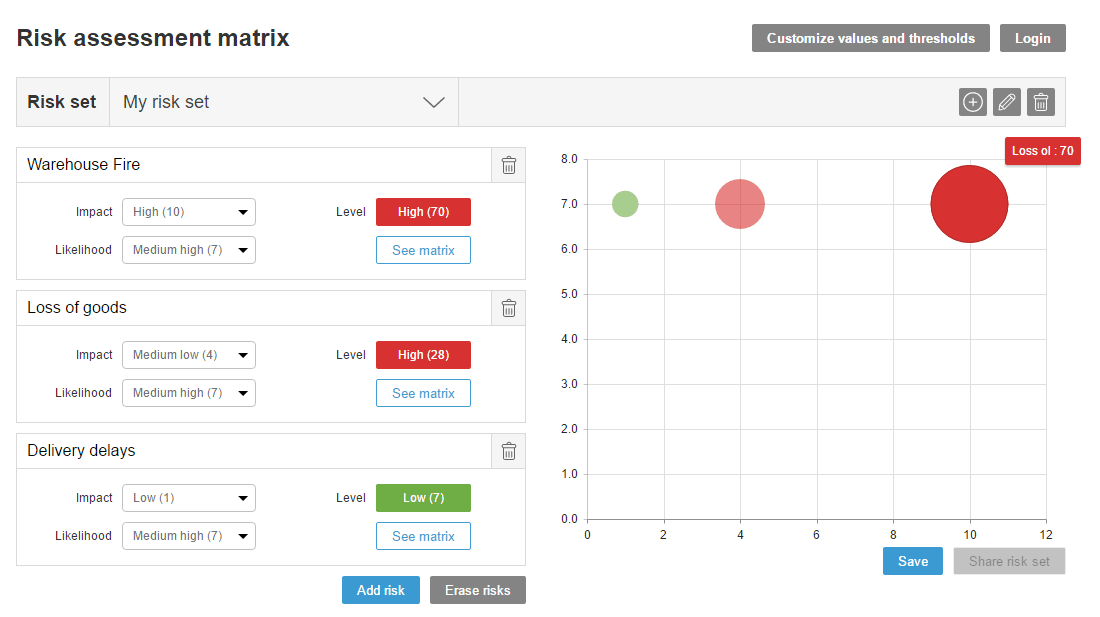
 Risk management has a specific place in protocols and risk management models. In this article we will discuss the six steps to controlling risk for risk managers, as broken down in the PMBOK: planning, identification, qualitative analysis, quantitative analysis, response planning and monitoring.
Risk management has a specific place in protocols and risk management models. In this article we will discuss the six steps to controlling risk for risk managers, as broken down in the PMBOK: planning, identification, qualitative analysis, quantitative analysis, response planning and monitoring. If you want to become a risk manager, you will have to combine two types of training.
If you want to become a risk manager, you will have to combine two types of training.